The digital landscape is constantly evolving, bringing with it a plethora of both exciting opportunities and daunting challenges. As organizations rely more on technology, they become increasingly vulnerable to cyber threats. One of the most pressing challenges in recent times has been the emergence of sophisticated attacks, notably the Octo Attack. This paper will delve into the nature of the Octo Attack, its implications on cybersecurity, and potential solutions to combat this growing threat.
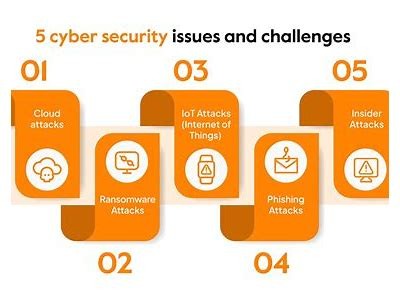
The Octo Attack is a multi-faceted cyber assault that involves several attack vectors and is designed to compromise the security of an organization thoroughly. Unlike traditional attacks that often focus on a single point of failure, the Octo Attack employs a strategic combination of techniques, including phishing, malware, and distributed denial-of-service (DDoS) attacks. This multifarious approach makes it particularly challenging for organizations to defend against.

As the Octo Attack becomes more prevalent, its implications for organizations grow increasingly serious. First, there is a significant financial impact. Organizations may incur massive costs due to downtime, remediation activities, and potential legal ramifications following a data breach.
Furthermore, the reputational damage resulting from such attacks can be catastrophic. Customers and stakeholders demand assurance that their data is safe, and any failure in this regard can lead to loss of trust and a declining customer base. In a world where social media amplifies the speed of information dissemination, negative news travels fast, causing lasting damage to organizational credibility.

To combat the complexities of the Octo Attack, organizations must implement a robust technological strategy. One effective measure is the adoption of advanced threat detection systems. These systems leverage artificial intelligence and machine learning to identify unusual patterns and behaviors within networks, allowing for faster and more accurate responses to potential threats.
Additionally, organizations should invest in a comprehensive cybersecurity framework that encompasses not only technology but also people and processes. This includes training employees to recognize phishing attempts, regularly updating software to patch vulnerabilities, and conducting security audits to identify gaps in existing defenses.
The regulatory landscape surrounding cybersecurity is continually evolving, with many governments enacting stricter laws to protect consumer data. Organizations must stay compliant with these regulations, as non-compliance can lead to substantial fines and legal repercussions. It is imperative that organizations familiarize themselves with regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA), among others.
Another crucial element in combating the Octo Attack is fostering a culture of cybersecurity within organizations. This involves educating employees at all levels about the risks associated with cyber threats and empowering them to act responsibly. Regular training sessions and awareness campaigns can help reinforce good behaviors and encourage a proactive approach to cybersecurity.
One of the most effective strategies against the Octo Attack is collaboration among organizations and within sectors. By sharing information about emerging threats and mitigation strategies, organizations can strengthen their defenses collectively. Initiatives such as Information Sharing and Analysis Centers (ISACs) provide platforms for organizations to share threat intelligence, fostering a community of mutual defense.
As attacks evolve, so must the technologies used to combat them. Emerging technologies such as blockchain, quantum computing, and zero-trust architecture hold promise for enhancing cybersecurity postures. Organizations should remain vigilant and open to adopting innovative solutions that can bolster their defenses against sophisticated attacks like the Octo Attack.
The rise of the Octo Attack poses significant challenges for organizations across various sectors. However, by understanding its implications and adopting proactive measures, businesses can enhance their cybersecurity defenses. A multi-faceted approach that includes technological solutions, regulatory compliance, employee education, collaboration, and investment in future technologies will be crucial in navigating the complex cyber threat landscape.
As we look to the future, it's clear that the fight against cyber threats like the Octo Attack will require a concerted effort. The stakes are high, and organizations must be prepared to adapt and evolve in response to the ever-changing digital environment. ```
转载请注明:willbet Free Online Games » wisdom of athena 1000 » Understanding the Octo Attack: Implications and Solutions for Cybersecurity Challenges Today